The Bvp47 - Technical Details II
Full Report Download: The Bvp47 Technical Paper II (PDF)
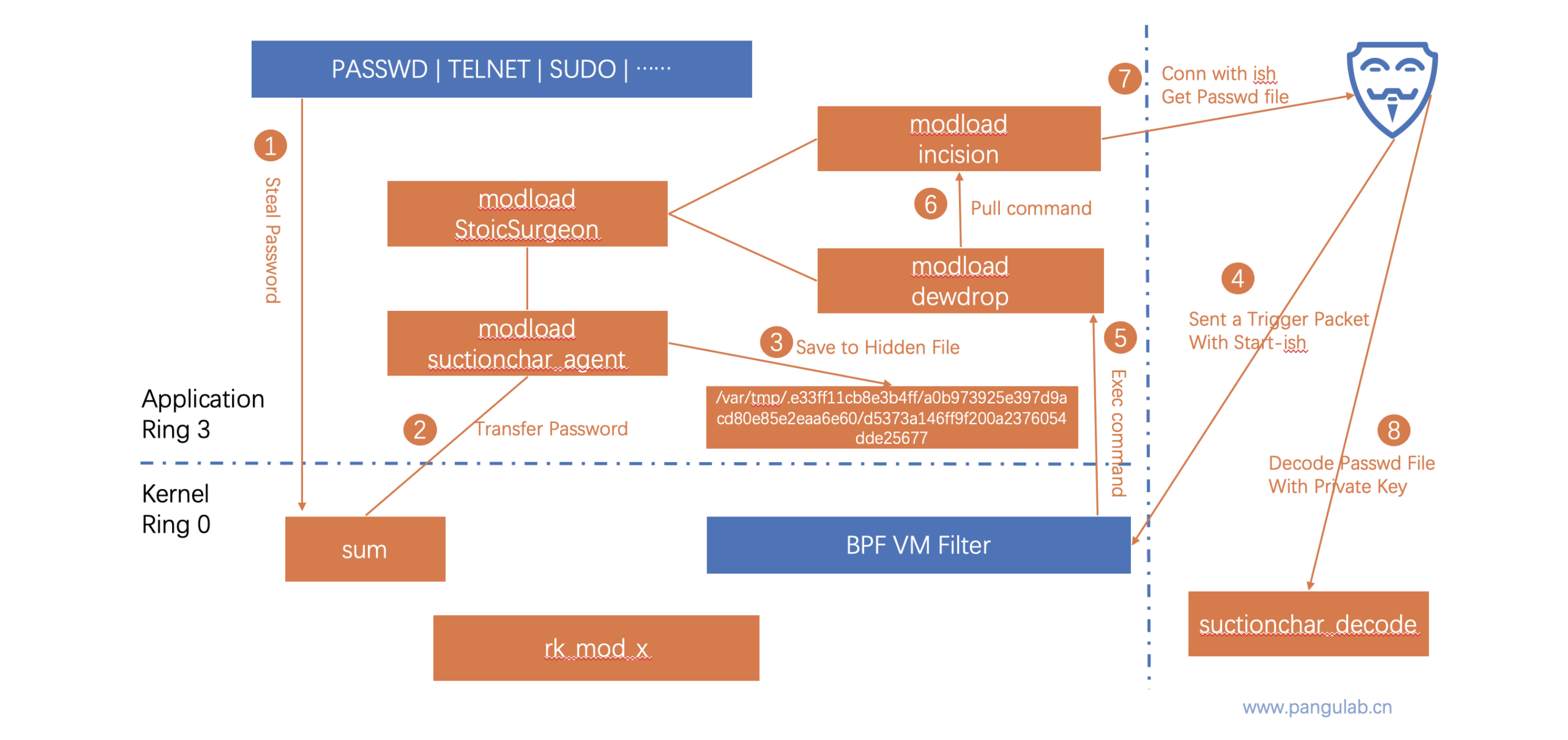
In report " Bvp47 – A Top-tier Backdoor of US NSA Equation Group " (Reference 1), Bvp47 is like a huge shell or compressed package, containing a total of 18 fragments. Pangu Lab gives attribution analysis and description of some technical details, such as BPF covert tunneling. However, there are still some other modules worth in-depth analysis. Those modules can either perform functions together as part of Bvp47 or be used independently.
In a forensic to Solaris system of one critical infrastructure in 2015, Pangu Lab extracted another sample, which survived independently on the Solaris platform and seemed to be closely related to Bvp47. After analyzing the leaked information, we confirmed that the content of the sample file was same to Suctionchar_Agent which was leaked from The Shadow Brokers. When executed with dewdrops, incision and other modules, it can easily steal password of target system, when user is executing commands like ssh, passwd, sudo. The file stored stolen passwords in target system also requires private key of RSA algorithm for decryption.
There is evidence that a large number of important domestic organizations were attacked by the Trojan horse program Suctionchar_Agent of the US National Security Agency (NSA), including Northwestern Polytechnical University. The Suctionchar_Agent has collected a amount of accounts and passwords in various countries around the world, and they can be queried at any time by the Operations Forces Tao of the NSA and "legally" entered the victim's information system.
The process of tracking Bvp47 is more like exploring a puzzle under fog. With the full cooperation of Pangu Lab and the National Computer Virus Emergency Response Center, this report will further illustrate parts of working method and execution logic of Bvp47, a top-tier backdoor platform, through analysis of Suctionchar_Agent, Dewdrop, tipoff, and Bvp47_loader.